Security related functions in the SmartFramework
The SmartFramework contains a series of security related functions (like authentication or authorization) typically required in business applications.
Those functions are designed to be extendable and customizable and allow integration with existing security functions.
Authentication
The standard login dialog LoginForm of the SmartFramework (actually the login dialog can also be used outside of the SmartFramework) uses SessionManager static class which calls into the current IAuthenticationService service instance for actually performing the authentication.
We provide two standard authentication mechanisms. But the list of authentication systems can be extended to match customer requirements.
Database Authentication Service
The DatabaseAuthenticationService class implements the IAuthenticationService Interface and provides authentication against a databases _user table. Database based authentication has come back into fashion with the introduction of multi-tenancy in the OpenEdge database.
The DatabaseAuthendicationService is a client side API (the client authenticates against the AppServer) and calls into the UserBusinessEntity method PerformDatabaseAuthentication.
The UserBusinessEntity performs authentication against a single database. The logical name of the authentication database is retrieved from the IConfigurationProvider service. By default the database name is read from either the .applicationsettings JSON file (OpenEdge 11) or .applicationsettings.xml XML file (OpenEdge 10) using the authenticationDb entry.
When the company that the user is trying to login against has a LoginCompanyTenantDomain value assigned, the user is authenticated as <username>@< LoginCompanyTenantDomain>. If not the user is authenticated as <username> only.
The method PerformDatabaseAuthentication returns the database client principal to the client which maintains it for future AppServer calls in the Context Dataset.
{
"appServerKeepAlivePeriod":"120",
"authenticationDb":"sports2000",
"homePageUrl":"http://www.consultingwerk.de",
"defaultPartition":"Default",
"maintainPasswordInSmartUser":"false",
"systemDescription":"Development",
"rollbaseRestApiUrl":"https://www.rollbase.com/rest/api/",
}
SmartUser Authentication Service
The AuthenticationService class implements the IAuthenticationService Interface and provides authentication against a password stored in the SmartUser table of the SmartDB.
The AuthenticationService performs authentication by trying to retrieve the SmartUser record with the given Login Company, UserName and password from the UserBusinessEntity.
When the record is found, the UserName is stored in the Context Dataset so that it is known on the client and on the AppServer in future calls.
When the authentication is done against the password stored in the SmartUser table of the SmartDB, then the User Maintenance form should also allow updating the password stored in this table (e.g. when creating new users). To allow the update of the password field in the SmartUserViewer the maintainPasswordInSmartUser setting in the IConfigurationProvider service needs to be set to “true”. By default this is read from either the .applicationsettings JSON file (OpenEdge 11) or .applicationsettings.xml XML file (OpenEdge 10).
{
"appServerKeepAlivePeriod":"120",
"homePageUrl":"http://www.consultingwerk.de",
"defaultPartition":"Default",
"maintainPasswordInSmartUser":"true",
"systemDescription":"Development",
"rollbaseRestApiUrl":"https://www.rollbase.com/rest/api/",
}
Authorization
Security Realms
Introduction
Security Realms describe a specific group of functions for which authorization is maintained using a centralized security assignment and enquiry system.
Security Realms are registered in the Security Realm Maintenance function of the SmartFramework.
Security Realms have the following attributes:
| Field Name | Description |
|---|---|
| Realm Code | A unique identifier of the security realm used when querying authorization using the ISecurityService or the Validate Class |
| Realm Description | A description of the security realm |
| Security Service | The service that defines the security realm specific data, used for the maintenance of the security assignment |
| Default Restricted | Defines if users are not allowed to use functions of this security realm unless they are granted or if they are allowed to use functions of this realm unless they are forbidden (grant/revoke) |
| Assignment Company Dependent | If the assignment of authorizations in this realm is stored per login company or for the whole system. Relevant for users or groups that exists in more than a single login company |
Security Realm Services
Security Realm Services provide the meta-data used during the maintenance of security assignment. Securirty Realm Services need to implement the ISecurityRealmService interface.
Overview of Security Realms
The SmartFramework provides a number of default security realms which are described in the following table:
| Realm Code | Realm Description | Used by |
|---|---|---|
SFS | Smart Field Enabled | Used by the SmartFieldAuthorizationProvider. The SmartFieldAuthorizationProvider implements the IFieldAuthorizationProvider interface and controls if data bound fields in SmartViewerControl derived user controls may be enabled for by the current user, i.o.W. the user is allowed to update the field value |
SFV | Smart Field Visibility | Used by the SmartFieldAuthorizationProvider. The SmartFieldAuthorizationProvider implements the IFieldAuthorizationProvider interface and controls if data bound fields in SmartViewerControl derived user controls shall be hidden. |
SMF | Smart Menu Function | Used by the MenuBusinessEntity to determine if the current user has access to a menu function of not. Used while reading menu structures from the SmartMenu table. |
SMT | Smart Message Translation | Used by the MessageBusinessEntity to validate if the current user is allowed to maintain message translations in the given language |
SST | Smart Security Token | General purpose function. Tokens can be used to protect specific application functionality. There is no default behavior for security tokens. Tokens may be queried using IsTokenRestricted method of the ITokenSecurityService implementation. |
STI | Smart Toolbar Security Item | Allows to disable specific toolbar buttons on toolbars or ribbons. Used by the ToolbarAuthorizationProvider which implements the IToolbarAuthorizationProvider service interface and is used by the SmartToolbarController. |
Smart Field Enabled and Smart Field Visibility (SFS and SFV)
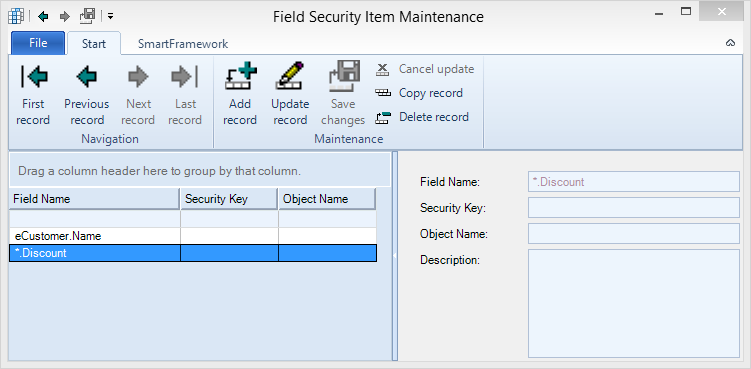
Before assigning authorization for field security relevant fields need to be entered in the Field Security Item Maintenance form.
Field Security Items are maintained using the following settings:
Field Name | Description |
|---|---|
Field Name | Either the fully qualified field name as known to the client (temp-table) or *.fieldname when the table name should be irrelevant |
Security Key | A security key of viewer controls. Allows to define field security for specific viewers only. Must match the “SecurityKey” attribute of the relevant viewer(s). Optional. |
Object Name | The name of the container (Form). Allows to define field security for specific forms only. Optional. |
Description | A description for the field security item. |
The same field security items are used to control if a user is allowed to update a field value and if a field may be shown.
Smart Menu Function (SMF)
Menu Functions are maintained using the Menu Function Maintenance.
Smart Message Translation (SMT)
Message Translation can be individually by turned on and off for any defined language in the system.
Smart Security Token (SST)
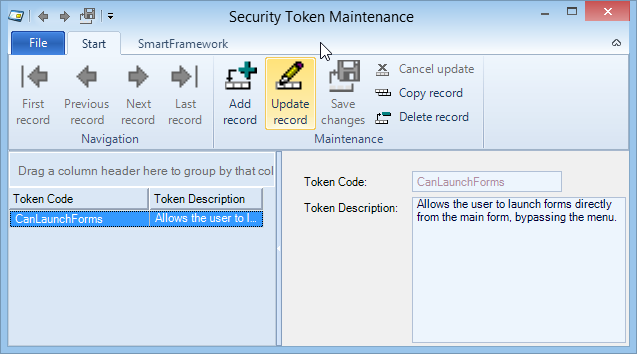
Security Tokens can be created using the Security Token Maintenance form.
Tokens are represented by a Token Code which is used to query the token authorization at runtime and a description.
Smart Toolbar Security Item (STI)
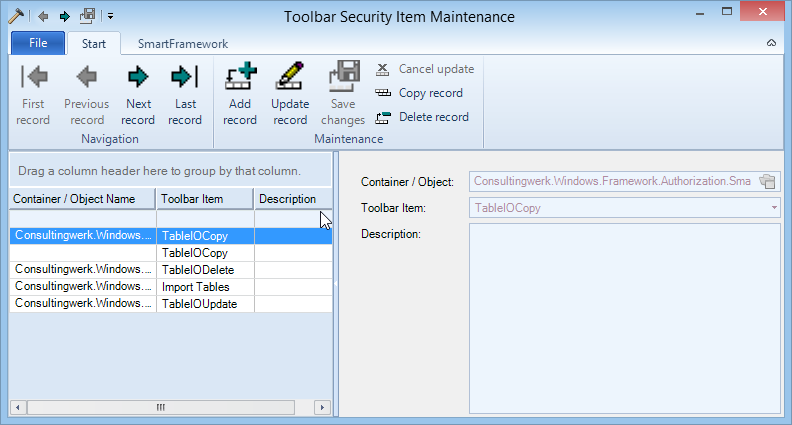
Toolbar Security Items are maintained using the Toolbar Security Item Maintenance form.
Toolbar Security Items are represented by the tool’s key (as known to the actual .NET Controls) and may be specific to a form or global for any form.
When adding records to the Toolbar Security Item Maintenance form users can select currently executed Forms using the lookup button on the Container / Object lookup. This will then also populate the Toolbar Item drop down list with the toolbar items of the selected form. User can select Forms or viewers and browsers in which case the authorization may be maintained for individual Viewers or Browsers within the Form.
Assigning Authorization for Security Realms
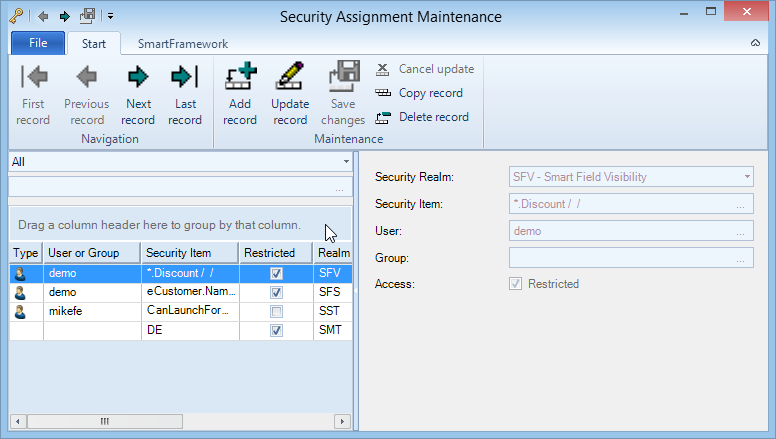
The central security Assignment Form can be used to maintain authorization for any user or any user group on any security item.
Using the combo-box and lookup above the grid control users can first select the security item (that is an item specified by an available security realm) to filter the list of existing security assignments.
Using the viewer security can be assigned for any users or group on any security item.
First, select the security realm for which you want to maintain authorization. Then select the security item using the lookup. The lookup properties have dynamically been changed based on the selected security realm.
A single security assignment record is always exactly for a single user or a single user group. You cannot create a single security assignment record that is valid for a user and a group.
For every security assignment record you control if it should be restricting (checked) or unrestricting.
The actual authentication for the user on the selected security item is based on the security realm’s default restricted property and the security assignment either for the user directly or the groups the user is member of. In general the rule applies that the closest security assignment will be effective.
Assigning Authorization for Menu Functions
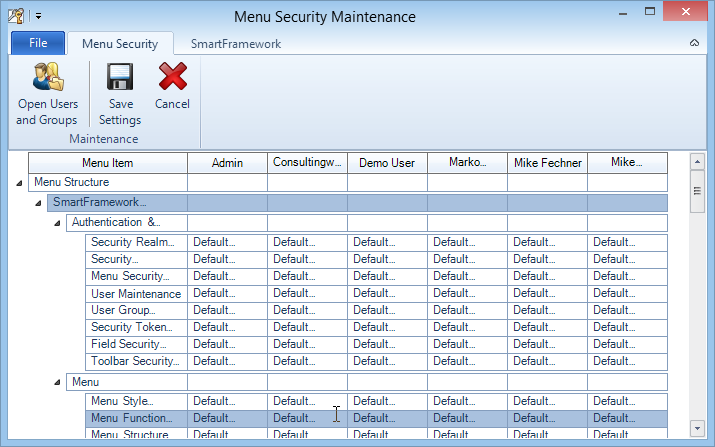
For the maintenance of menu function authorization a more specialized alternative data entry screen has been implemented. The Menu Security Maintenance form allows to select a number of users and or groups and allows the maintenance of menu function authorization
After selecting a number of users or user groups an administrator may change or create the security assignment for menu functions based on the actual menu structure using the drop downs in the tree view columns.
The drop downs provide three values:
Restricted | Creates an security assignment entry with restricted = TRUE |
Unrestricted | Creates an security assignment entry with restricted = FALSE |
Default | Removes an existing security entry, resulting in the next available default setting |
Menu Visibility for User Groups
Closely related to access to menu functions is the visibility of menus for groups of users.
For this purpose the Menu Maintenance allows the assignment of user groups to menu structures.
This dialog allows to assign any menu structure node to any user group. Users of that user group will have access to this menu structure as a top level menu structure.
Security Service
When not provided by specialized services (such as for Security Tokens), the ISecurityService implementations allow developers to query the authorization for the current user for a given security item. The security item is identified by the realm code and the unique identifier of the security item in query (as defined by the security realm service).
There are two security services available:
Server side security service implementation that implements the actual authorization logic based on assignments for the user, the groups the user is member of or the security realm default | |
Caching client side version of the Security Service. |
The primary method of the ISecurityService is the method IsRestricted which can be used like this to return if a user does not have access to a certain function.
DEFINE VARIABLE oSecurityService AS ISecurityService NO-UNDO .
oSecurityService = {Consultingwerk/get-service.i Consultingwerk.SmartFramework.Authorization.ISecurityService} .
/* ... */
IF VALID-OBJECT (oSecurityService) AND oSecurityService:IsRestricted ("SMF":U,
eSmartMenu.FunctionGuid) THEN NEXT .
Validate Class
The Validate Class does also provide a simple API to query authorization during the validation of updates in a Business Entity. The method IsNotRestricted validates that the user has authorization for a specific data item identified by a security realm code and the value of the field passed to the Validate:IsNotRestricted method.
FOR EACH eSmartMessage ON ERROR UNDO, THROW:
Consultingwerk.OERA.Validate:IsNotRestricted (BUFFER eSmartMessage:HANDLE,
"LanguageGuid":U,
"SMT":U,
MessageFormatter:GetMessage ("SFR":U, 200)) .
END.
Additional Security Hooks
Request Authorization Provider
The request authorization provider is an optional service. The service must implement the IRequestAuthorizationProvider interface and will be used by the ServiceInterface when a service is registered against that interface.
The request authorization provider allows to verify requests to the backend of the framework. As any call needs to pass the service interface this allows to reliably inject of any kind of security checks such as authorization for specific business entities or tasks.
See the interface description for further details.
Server Session Activator
The server session activator is not truly a security feature but security related. It is responsible for restoring the session context on the backend. The server session activator reacts on the Activate and Deactivate events of the ServiceInterface class.
We do not provide an interface for the server session activator. We do however provide a reference implementation in the form of the ServerSessionActivator which can also be loaded from a services.xml file. This class does for instance restore the SessionManager properties and imports the client principal of the Context Dataset into the current security context.